SIM card and smart card in one
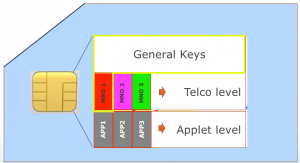
We don’t see the E-SIM as being a SIM card in your phone – first and foremost, we see it as an applet with the functions of a SIM card on a smart card. Education and research institutions currently use smart cards for student and employee cards. The E-SIM allows smart card functionality to be expanded by adding a SIM card functionality, and to integrate this into the phone. This means that apps running on your phone, for security purposes, are using the smart card with integrated E-SIM.

The E-SIM has its own management and maintenance methods, which have been prescribed by the telecommunications industry. Telecommunications profiles are added to the E-SIM for telephone, SMS/M2M and data communication purposes. Today, SIMs use these profiles to authenticate users and steer phones to the correct mobile network. The difference with the E-SIM is that it offers flexibility: a profile doesn’t have to be placed on a smart card in a factory, as it can be uploaded. It can later be replaced by a profile from another telecommunications provider, which means that users will use the new provider’s mobile network from that point on.
By placing a telecommunications profile on a smart card that is also used for the technical functionalities offered by the student and employee card, you open the door to a whole host of integrated functionalities. You can add functions to a smart card that, for example, provide access to buildings, printers, lifts, coffee machines, but you also have the option of adding access to eduroam. The applications on the phone will then outsource the security functions to the smart card, where the telecommunications profiles are also located. All sorts of applets are possible here, meaning a wide range of applications becomes available.
Better security than a phone
A smart card can be used as a sort of vault where you keep your passwords. In essence, what happens is that an application on the phone sends a ‘challenge’ to the applet on the smart card, which then sends a response. Should the right response be received, the security is deemed to be acceptable. This is more secure than saving credentials on your phone – if someone finds your phone, they can then carry out a brute-force attack to crack your password. This may result in the theft of your digital identity (used by an application). This is much harder to do with a smart card, as it has been specially designed and set up to prevent others from being able to retrieve the secret information.
On the way to a joint security architecture
In order to use the smart card’s ‘vault functionality’ correctly, SURF suggests developing a joint hardware security architecture with their member institutions. The technical and functional requirements for the hardware (the smart card) should be documented in this architecture. By making these choices together, you can convince suppliers of parking facilities, cards and printers to name a few, but also software developers to use this architecture for their products. You can then lower your procurement costs, for instance, and you will only need one card (or your phone). But there is another, more important benefit: as all the suppliers fulfil the joint architecture specifications, we can audit the whole system for security aspects. In addition, we are able to take better action in the event of security issues: with everyone using the same architecture, we can provide information on solutions centrally in the event of hacks, for example.
Integrating a smart card… or not
As mentioned above, it is possible to integrate this smart card into a phone (after all, the ‘E’ in E-SIM stands for ’embedded’), but you don’t have to. It can also be placed in other types of devices, such as smart watches, machines and toys. By adding the NFC functionality to the smart card, you can place it in a card the size of a credit card which is then used just like the traditional student or employee card. You can still use the smart card as a SIM card later: simply remove the smart card element from the card, place it in the SIM card slot of an Android phone and then push a user profile to it for communication purposes. In the pilot we previously carried out with the E-SIM, we showed that telephones operate with a regular SIM that obey all E-SIM functionalities and capabilities. Hence the E-SIM doesn’t necessarily need to be integrated into the phone.
The advantage of placing a smart card in a phone is that it can always be managed remotely as long as there is a network connection. The smart card is managed via a user interface, while applets can be installed via an applet store should you so wish. Institutions can do this centrally within their own security domain.
Read also
- Blog 1 of this blog series: Radical changes needed in campus ICT services
- Blog 2 of this blog series: Indoor coverage 2.0: working together on in-building communication services on campus
0 Praat mee