Eyle Brinkhuis
Eyle werkt 5 jaar bij SURF en is vanuit het Jong Talent programma… Meer over Eyle Brinkhuis
Institutions want to make their applications more secure by using multi-factor authentication. SURFnet has developed a plug-in for Microsoft ADFS that allows you to use SURFconext Strong Authentication as a second authentication factor for applications connected to ADFS. We have now started a pilot that you can join.
Since 2015, SURFconext Strong Authentication has made it possible to make cloud services connected to SURFconext more secure by using a second factor, in addition to the username/password combination. Until recently, using SURFconext Strong Authentication was not possible for applications connected to Microsoft Active Directory Federation Services (ADFS).
A SURFnet survey showed that institutions feel that this is desirable. For example, some applications connected to ADFS allow users access to privacy-sensitive data. Other applications manage critical business processes. Institutions want better security for these types of sensitive applications.
SURFnet set to work to meet this demand. We wrote a Multi-Factor Authentication (MFA) plug-in for ADFS. This plug-in allows multi-factor authentication via SURFconext Strong Authentication for applications connected to their own ADFS.
Many institutions connected to SURFconext use ADFS. ADFS makes it possible to set up a federated identity with SURFconext, for example. This allows the institution’s users to log on to SURFconext with the username and password they use for their own institution.
ADFS also offers the option of multi-factor authentication. The first factor (username and password combination) is still handled via Microsoft Active Directory Domain Services (ADDS). The second factor requires a plug-in for ADFS. The plug-in we developed ensures that SURFconext Strong Authentication handles the second factor.
The multi-factor authentication of the applications then occurs as follows:
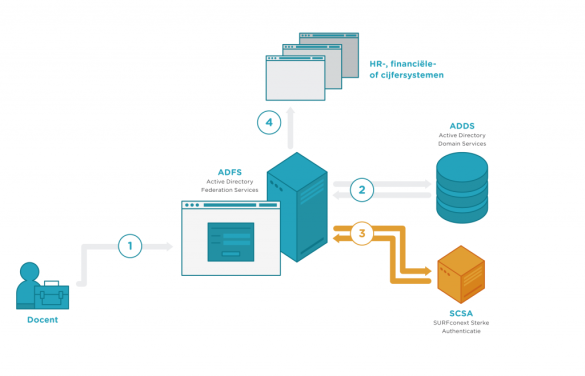
In the past few months, a first pilot using this plug-in was set up in collaboration with Windesheim University of Applied Sciences and Clusius College. These institutions have installed the ADFS plug-in in their test environment and tested SURFconext Strong Authentication with their applications.
The use of the plug-in was very successful in the initial pilots. It makes it possible for multi-factor authentication to be to required or not required for ADDS security groups for each federated application. This scenario turned out to be very workable in practice, so Clusius and Windesheim were enthusiastic about the plug-in.
The ADFS MFA plug-in uses a standardised SURFconext Strong Authentication interface. Other authentication systems used at institutions can also use this SURFconext Strong Authentication interface. Institutions have already connected in the past from Citrix Netscaler and F5 BIG-IP. We have also done this now with ADFS by using a plug-in.
The pilot period for the plug-in will continue until April 2018. During this period, support will be provided to allow institutions to find out whether this is something they want. If you are interested in using the plug-in, or if you want to use SURFconext Strong Authentication with another existing authentication system, please contact the SURFconext team at info@surfconext.nl.
Eyle werkt 5 jaar bij SURF en is vanuit het Jong Talent programma… Meer over Eyle Brinkhuis
0 Praat mee